Network Configuration & Change Management using StableNet®
StableNet® – NCCM & VLM White Paper
This White Paper will provide you with an insight on how to address these mission-critical tasks in your network infrastructure.
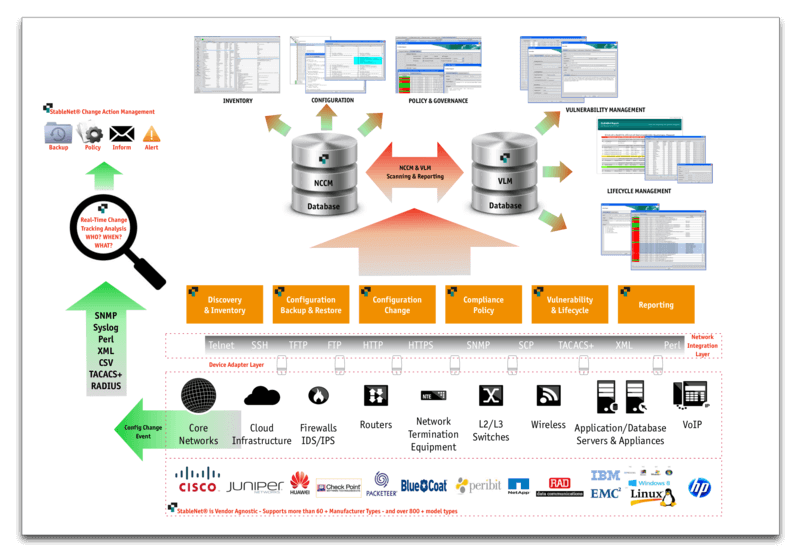
Discovery & Network Inventory
Section 2.1 of the White Paper provides greater insight into the key features around the hardware, software, and network discovery. Detailed inventory reporting can be produced and scanning of lifecycle and vulnerability announcements can be analyzed and reported against
Device Configuration Backup
Device Configuration Backup Key Feature Table:
|
Feature ID |
Feature Type |
Feature Description |
Feature Supported |
|
#1 |
Multi-Protocol support. |
Multi-protocol functionality is enabled to support multi-access to a multi-vendor infrastructure environment. Protocols supported include: ‘Telnet, SSH-Telnet, TFTP, FTP, HTTP, HTTPS, XML, Perl, SNMP, SCP’ |
+ |
|
#2 |
Authenticated integration. |
StableNet® fully supports authentication integration into industry standard authentication systems i.e. ‘TACACS+, RADIUS, LDAP’ the ability to integrate with other bespoke authentication systems is possible on request. |
+ |
|
#3 |
Bulk and scheduled backup functionality. |
StableNet® has a comprehensive in-built auto-scheduler whereby the configuration backups of an infrastructure can be configured to requirement & schedule. Backups can range from a single device to bulk backups of specific or entire infrastructures. |
+ |
|
#4 |
Additional scripting for CLI command inclusion. |
Additional scripting for CLI command inclusion into any backup job can also be fully customized i.e. Performing a series of ‘Show’ commands as part of the backup process for usage, tracking and health purposes. |
+ |
|
#5 |
Text file-type supported. |
Text file-type backups fully supported. Vendor types that use text based backups include Cisco, Juniper, Huawei, Brocade etc. |
+ |
|
#6 |
Binary file-type supported. |
Binary file-type backups fully supported. Vendor types that use binary based backups include Ixia, Bluecoat, F5 Networks etc. |
+ |
|
#7 |
Archived storage support. |
Full support for archiving of all backed-up configuration is optional, storage requirements need to be taken into consideration. |
+ |
|
#8 |
Config backup compare. |
Powerful compare configuration difference (config-Diff) is an enabled feature within the StableNet® NCCM allowing you to visualize what has been changed from the previous config to date, or simply comparing the start-up config to the running config etc. Additionally, any other pre-scripted config backup captures i.e. ‘Show’ type command config collections can also be compared in order to track usage, health, and degradation over time. |
+ |
|
#9 |
Backup process operation notification/alerting. |
When a backup job starts, ends or maybe fails operational and service type personnel may be required to be notified. Notification and alerting of backup events can be communicated via Email, SMS (if you have an available SMS gateway), and via the StableNet® GUI & Portal. |
+ |
|
#10 |
Reporting & analytics. |
Customized configuration backup reports can be created via the reporting theme within the StableNet® GUI. These reports can be HTTP or PDF type reports and are available to view either via the portal dashboard, or by simply opening the PDF document. |
+ |
Configuration Change Management
Enabling of Real-Time Configuration Change Detection
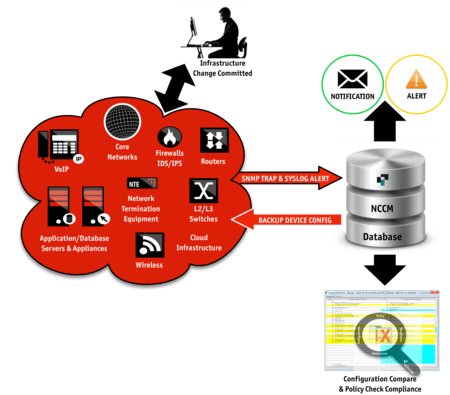
Bulk Configuration Change
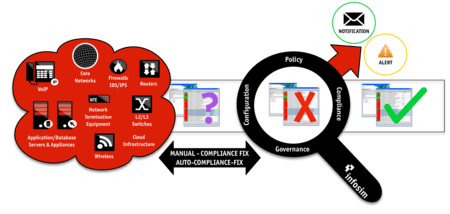
Policy Checking
The policy compliance and governance engine within the NCCM module of StableNet® allows corporations to create policies electronically in order to scan/analyze configurations of the infrastructure environment so as to produce accurate and timely compliance and violation reporting analytics.
Download: Send a request
Xantaro Relies on StableNet® – For Even More Powerful Network Monitoring in the NOC
The Xantaro Group is taking its service and monitoring offering to the next level: From now on, the powerful network…
Secure Automation of Electrical Infrastructure in Spain – StableNet
Empowering secure, automated 5G and IoT rollouts across Spain’s critical infrastructure with Infosim® and NEVERHACK…
Tolly Report 2025: Unified Network Configuration & Change Management with StableNet®
StableNet® by Infosim® delivers efficient, secure, vendor-independent NCCM for today’s complex it networks…

Software
Made in Germany


