NCCM, Vulnerability and End-of-Life with StableNet®
Excecutive Summery
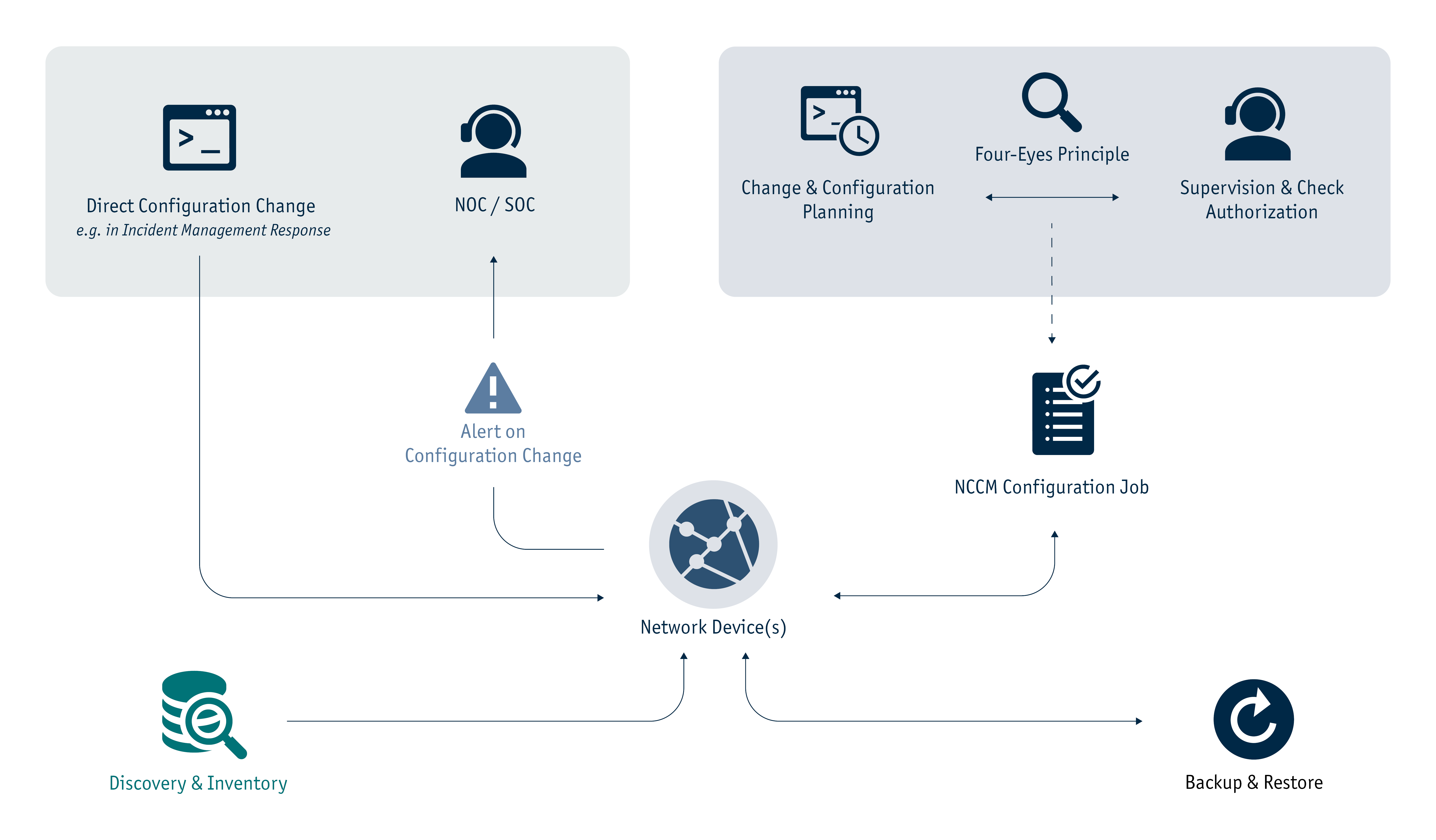
Beyond discovery, StableNet®‘s NCCM solution integrates automated backup and restore, policy compliance checks, and change Management processes into a cohesive, streamlined framework. Through templated configuration deployments, job scheduling, and adherence to best practices like role-based access control, StableNet® ensures that changes are repeatable, authorized, and auditable. Furthermore, its LifeCycle and vulnerability management features keep the infrastructure secure and aligned with vendor updates. In essence, StableNet®‘s automation-driven approach transforms NCCM from a reactive, resource-intensive task into a scalable, reliable, and policy-compliant operation.
The complete 16-page White Paper is only one click away
Fill out the form and have it emailed to you immediately as a PDF.
The Customer Pilot Hub – A Further Step Towards Open Innovation
With the new StableNet® 26 Annual Release, the Innovation Lab is introducing a new extension: The Customer Pilot Hub.
Getting Started with Data Center Environmental Monitoring
Data center environmental monitoring refers to the monitoring of environmental conditions in a data center, such as temperature and humidity…
Shaping sustainable and resilient communication networks
Infosim® & SKOOR are part of the Celtic Next project SUSTAINET-Advance. Read this blog post to find out more.

Software
Made in Germany