SDN/NFV-enabled Security Architecture for fine-grained Policy Enforcement and Threat Mitigation for Enterprise Networks
Demo at SIGCOMM 2017
Today, network security in enterprises is mainly enforced by firewalls guarding the perimeter of the network against an ever-increasing number of cyber threats. However, once the perimeter is breached attackers and malware can easily compromise additional hosts as we have seen in the recent outbreak of the WannaCry worm.
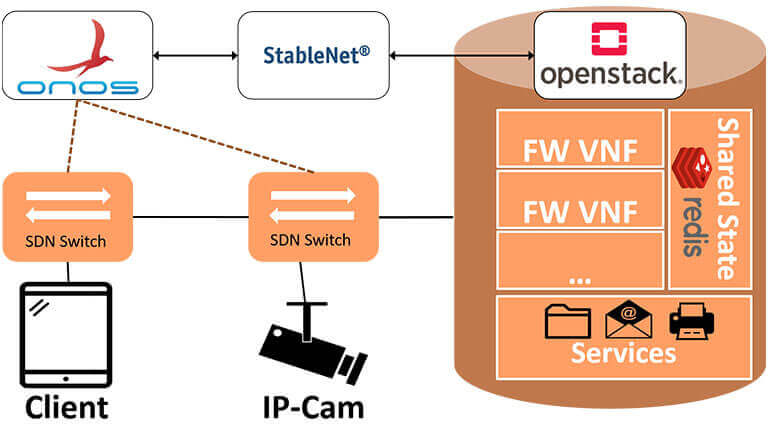
A complimentary approach to alleviate these threats is to quarantine malicious hosts on a network level. To accomplish this, a fine-grained flow selection and security control is needed which can be provided by architectures like Software-Defined Networking (SDN) and Network Function Virtualization (NFV).
As one of the authoring partners of this demo at the renown ACM SIGCOMM conference, we demonstrate the prospects of seamlessly integrating SDN and NFV based security operations into the existing enterprise network infrastructure to provide state-of-the-art stateful firewalling for advanced packet filtering as well as on-demand fine-grained flow separation and isolation for the exterior and interior network.
StableNet® provided by Infosim® and the extensions made to it play one of the key roles in this demo. Not only does StableNet® monitor all critical systems within the demonstrator, but the shown scenarios also demonstrate how our solution is capable of consolidating modern SDN and NFV environments as well as legacy network infrastructures.
Research Partners: University of Würzburg, TU Munich, genua GmbH, Infosim®
The Customer Pilot Hub – A Further Step Towards Open Innovation
With the new StableNet® 26 Annual Release, the Innovation Lab is introducing a new extension: The Customer Pilot Hub.
Getting Started with Data Center Environmental Monitoring
Data center environmental monitoring refers to the monitoring of environmental conditions in a data center, such as temperature and humidity…
Shaping sustainable and resilient communication networks
Infosim® & SKOOR are part of the Celtic Next project SUSTAINET-Advance. Read this blog post to find out more.

Software
Made in Germany


