
Regular posts on all things around automated network & service management

Features, trends and new product development
6 Steps to a Successful Network Audit that Saves You Time and Resources (with Checklist)
Network audit software can be instrumental in helping operators of large networks ensure compliance and enhance security. It is a critical component to proactive network and service management.
However, most solutions are limited in their functionality, require learning yet another tool, and lack a focus on automation.
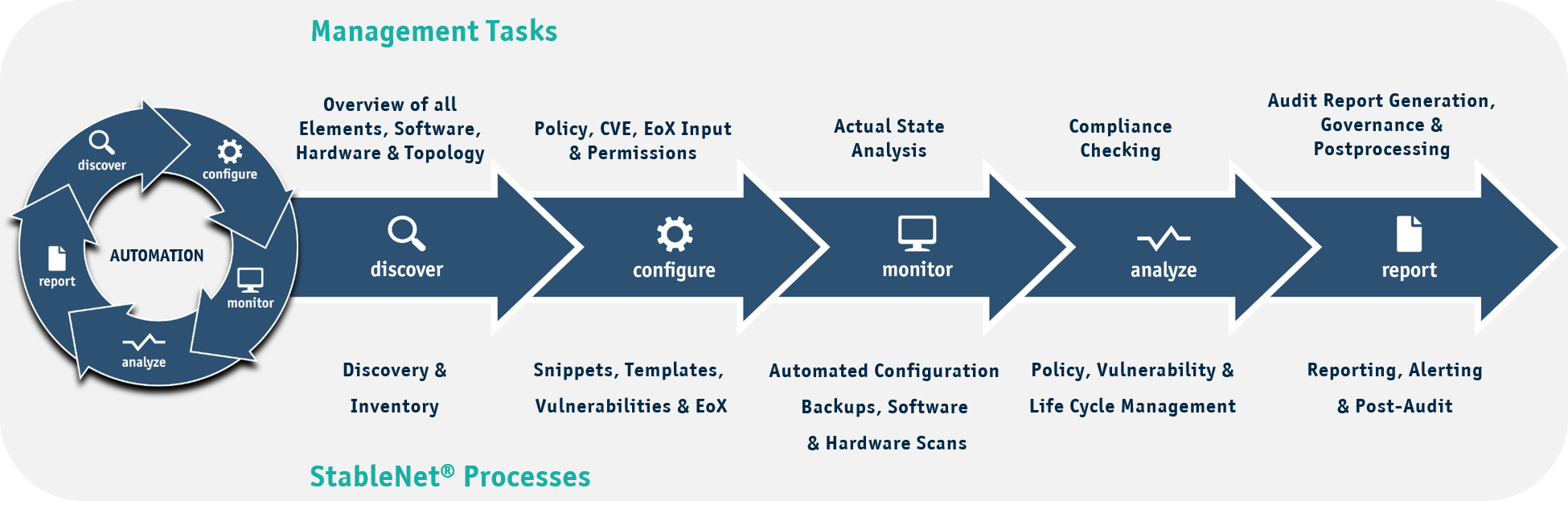
A network and service management platform like StableNet® provides an ideal opportunity to consolidate a wide range of tasks, from discovering your multi-vendor environment to automated root cause analysis. By combining and automating the management of complex network environments, StableNet® is a scalable solution whether you are using legacy systems, cloud-based infrastructures, or a combination of various technologies.
By combining all of this with lifecycle management, vulnerabilities, and compliance and policy checking at regular, automated intervals, you not only free up network operation resources but benefit from a holistic approach to network management with a single GUI that runs the entire gamut of tasks that you need.
6 steps to success – most important aspects of a network audit
Step 1: Discovery and Inventory
Having an overview of your own inventory is the basis for every network audit and the starting point for further measurements and analyses. This step is essential to be able to make general statements about the condition of your network. After all, you can’t manage what you can’t see.
Step 2: Risk Assessment
Another key point is to find and close potential network security gaps. On one hand, this includes identifying the devices in your network that have reached the End-of-Service (EoS) or End-of-Life (EoL) stage in their lifecycle or will do so in the near future. On the other hand, it involves analyzing your network for currently published vulnerabilities.
Step 3: Configuration & Policy Compliance
Configurations must be scanned, analyzed and compared on a regular basis. They determine compliance with established policies and regulatory standards (such as PCI-DSS, ITIL, NSA, etc.). Regularly checking and, if necessary, reconfiguring them is therefore essential for demonstrating compliance.
Step 4: Change Management
It is quite normal that there are changes in your network. An effective network management platform allows you to track those changes to see who did what, when it was done, and of course allowing for rollbacks and restorations in the case of problems. That’s why regular back-ups and network configuration checks are an important part of an audit. Especially in the case of misconfigurations, they can not only be quickly detected but also quickly restored to an older working state.
Step 5: Access Control
To ensure security on your network, access rights must be defined. This includes managing and regularly reviewing roles, user accounts, and permissions to prevent unauthorized people from accessing your network.
Step 6: Compliance Reports
At the end of each audit, the complete documentation of the process is crucial not only for the internal management level alone, but above all for external organizations to guarantee compliance with guidelines and standards.
Work smarter not harder – Automation as the key to successful network audits
Now you know what the most important aspects of a network audit are.
The only question that is left is how you want to perform such an audit. One possibility, of course, is to perform this process manually. However, you won’t get very far here, since modern networks in especially large organizations are characterized by their high complexity of network components and topologies. A manual physical audit of network devices and their configurations would therefore be extremely time-consuming. In addition, manually performed audits often require in-depth expertise, particularly in the area of industry-specific standards and guidelines, and a very thorough and accurate way of working, so this process is often accompanied by human error.
To reduce the resources and time required for network audits, organizations often use network management tools, automated scanning tools and network monitoring systems. These technologies help streamline the audit process, automate routine tasks, and provide insight into network health and security.
Therefore, performing a network audit manually is hardly an option. The better way is to automate your audit process with a network management system.
Network Audit Tool – Automated Network and Service Management Solution with StableNet®
Through this consolidated toolset, you can not only perform a network audit, but StableNet® also provides you with a direct solution to some of the problems it uncovers.
To have a secure network, not only regular audits should be part of the routine, but also the continuous maintenance of your service, which can only be achieved through a comprehensive network management.
If you want to read even more information around StableNet®‘s network audit solution, take a look at our latest use case around this topic. Furthermore, we have also compiled a network audit checklist for you with the most important aspects of a network audit.
Network Audit Checklist
If you are planning a network audit, or are simply frustrated with the amount of manual resources required for the activity, we have put together a checklist for you that will lay out some of the key steps and also make it clear how useful automated processes can be.
Use Case: Network Audits Made Easy
Stay compliant and safe with a holistic network management platform that does it all. From End-of-Life to automated policy checking and reporting, see how StableNet® not only allows you to manage your cross-technology network but to safeguard it (and you) for peace of mind and sustained growth.

Melanie Weber
Marketing Project & Content Creation Manager @ Infosim® GmbH & Co. KG

Software
Made in Germany
