
Regular posts on all things StableNet® related from a sales, techie, or marketing perspective

Features, trends and new product development
Two-Factor Authentication in StableNet®
In this blog post, I’d like to quickly introduce what two-factor authentication is, why it’s so important, and provide a few use cases in which its immanent inclusion as a safety measure is critical and/or required for compliance. Finally, we will have a quick look at its integration in the upcoming annual release of StableNet® 25 (in the rich-client and also the web-based StableNet® Portal).
Understanding Two-Factor Authentication (2FA)
The Value of Two-Factor Authentication in Network Management
In network and service management platform solutions such as StableNet®, the stakes are high. Nowhere was this more prevalent than witnessing the fallout from the cyber attack on SolarWinds (forcing them to rename their MSP software to “N-able”) at the end of 2020. Unauthorized access can lead to severe consequences, including data breaches, service disruptions, and compliance violations. 2FA can alleviate this in a few ways:
Compliance with Regulatory Standards
For organizations managing sensitive data, regulatory compliance is not optional. Standards such as PCI DSS, BSI IT-Grundschutz, and KRITIS mandate rigorous security measures to protect data and ensure operational integrity. Implementing 2FA is a critical step in meeting these requirements.
Enhanced Security
The primary advantage of 2FA is the substantial increase in security it offers. By requiring a second form of authentication, the likelihood of a successful attack is greatly reduced. Even if an attacker acquires a user’s password, they would still need the second factor—such as a mobile phone or hardware token—to gain access.
Mitigating Phishing Attacks
Phishing attacks are a common method used by cybercriminals to steal user credentials. 2FA mitigates the risk associated with these attacks because the attacker would need more than just the stolen password to succeed. The additional authentication step acts as a significant barrier against such threats.
Some Use Cases: Compliance Requirements and Two-Factor Authentication
PCI DSS (Payment Card Industry Data Security Standard)
PCI DSS is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. One of the key requirements of PCI DSS is the implementation of strong access control measures, including 2FA. Specifically, PCI DSS Requirement 8.3 mandates the use of multi-factor authentication (MFA) for all non-console administrative access and for all remote access to the network by personnel, administrators, and third parties.
Implementing 2FA helps organizations comply with these requirements by ensuring that access to sensitive payment systems is tightly controlled and that users are properly authenticated before gaining access.
BSI IT-Grundschutz (Germany)
The BSI IT-Grundschutz (Basic Protection) is a comprehensive set of standards and guidelines issued by the German Federal Office for Information Security (BSI) to help organizations establish a robust security management system. It emphasizes the importance of securing access to IT systems and data through measures such as 2FA.
By integrating 2FA into StableNet®, organizations can enhance their compliance with BSI IT-Grundschutz by adding an additional layer of security that helps prevent unauthorized access and ensures that only authenticated users can manage critical infrastructure components.
KRITIS (Critical Infrastructure Protection)
KRITIS refers to the protection of critical infrastructures, which are essential for maintaining societal systems, including the energy supply, water distribution, and healthcare services. The security of these infrastructures is paramount, and stringent measures are required to protect them from cyber threats.
Implementing 2FA in StableNet® aligns with KRITIS requirements by providing robust access control and ensuring that only authorized personnel can make changes to critical infrastructure systems. This helps prevent potential disruptions caused by cyberattacks and enhances the overall resilience of critical infrastructure operations.
The Role of Two-Factor Authentication in StableNet®
- Ensuring Secure Access: 2FA ensures that only authenticated users can access the network management console, reducing the risk of unauthorized access.
- Protecting Sensitive Data: By adding an extra layer of security, 2FA helps protect sensitive data from breaches and unauthorized alterations.
- Maintaining Operational Integrity: With 2FA, your organization can maintain the integrity of network operations by preventing unauthorized changes to network configurations and settings.
- Facilitating Compliance: 2FA helps meet regulatory requirements, thereby avoiding potential fines and reputational damage associated with non-compliance.
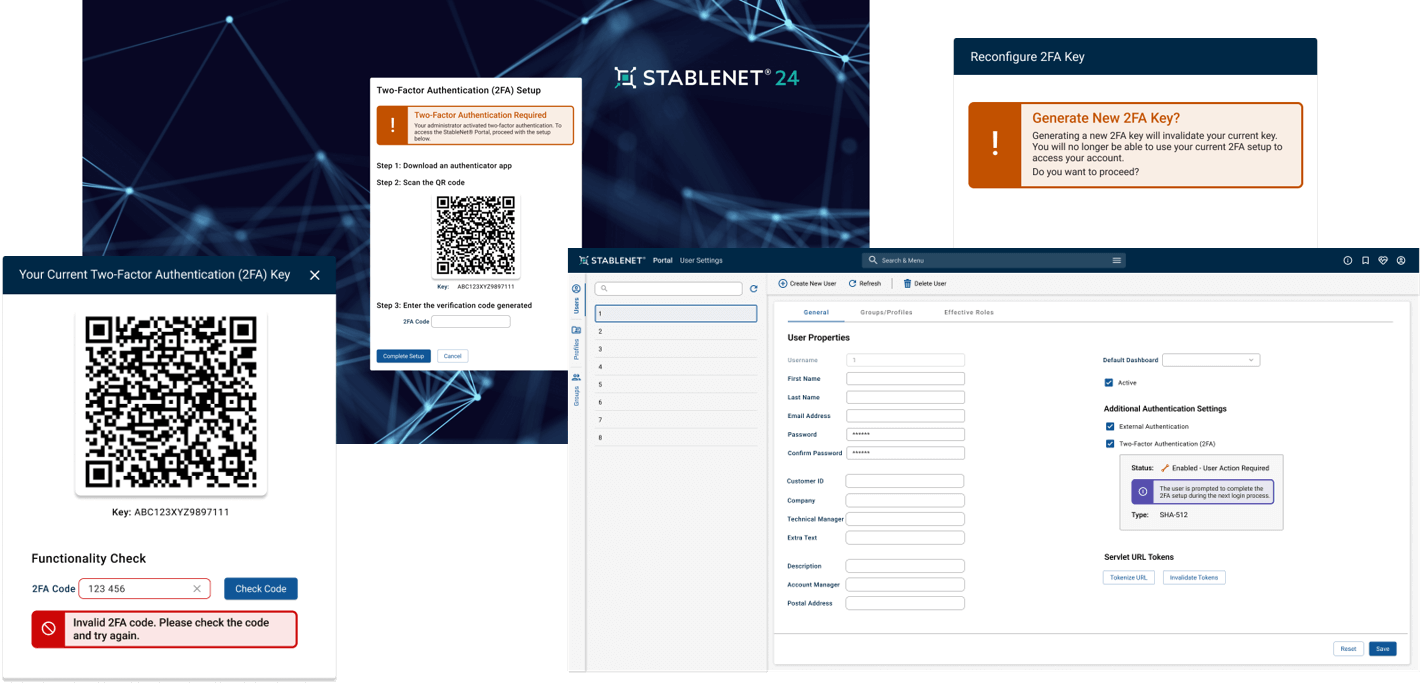
StableNet® 25 and Two-Factor Authentication
We look forward to your feedback and, as always, are ready with an open ear for continued feature requests. After all, our long-term success has is large part been because we listen to what you need and deliver the solutions you require.

Dr. David Toumajian
Director of Marketing @ Infosim® GmbH & Co. KG

Software
Made in Germany
